In the intricate tapestry of the internet, where legitimate businesses thrive and communities flourish, there exists a shadowy underworld, concealed from the prying eyes of the mainstream. Here, in the dark corners of cyberspace, dwell platforms like bclub.cm, silently beckoning to those willing to delve into the illicit trade of dumps and CVV2.
Imagine a clandestine marketplace where stolen credit card data, known as dumps, and their corresponding verification codes, CVV2, are bought and sold with eerie efficiency. This digital black market operates beyond the bounds of legality, fueling a clandestine economy that preys on unsuspecting individuals and institutions.
At first glance, the uninitiated may question the allure of such nefarious endeavors. Yet, for those immersed in the world of cybercrime, the appeal lies in the promise of easy money and anonymity. With just a few clicks, aspiring fraudsters gain access to a treasure trove of financial information, ripe for exploitation.
But beneath the veneer of easy riches lies a landscape fraught with peril. For every would-be cybercriminal hoping to strike it rich, countless adversaries are lurking in the shadows, ready to exploit vulnerabilities and sow chaos. From law enforcement agencies wielding the sword of justice to rival hackers seeking to protect their own turf, the dangers are ever-present.
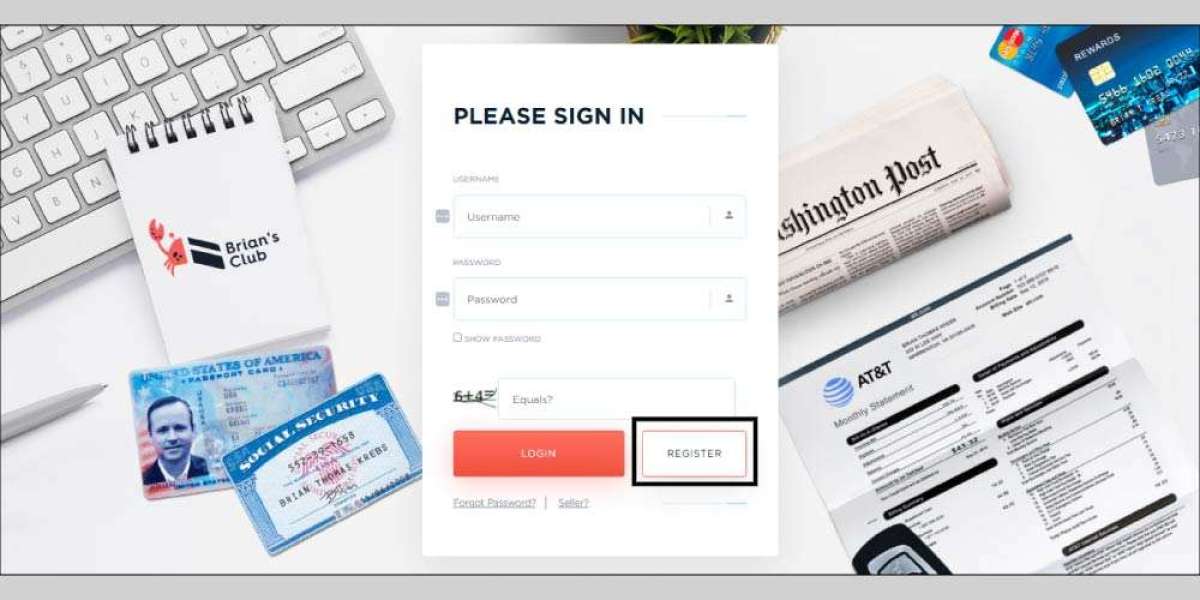
In this murky realm, the concept of trust takes on a whole new meaning. On platforms like bclub.cm, where anonymity reigns supreme, establishing credibility is paramount. Reputation is currency, and those with a proven track record command respect and influence. Yet, even the most seasoned veterans must tread carefully, for betrayal and deception lurk around every corner.
The mechanics of this underworld are as complex as they are insidious. At the heart of it all are the dumps – stolen credit card data harvested through various means, from sophisticated cyber-attacks to simple skimming devices. These digital gold mines contain a wealth of information, including cardholder names, account numbers, expiration dates, and CVV2 codes.
But the journey from data theft to financial gain is not without its obstacles. Enter the CVV2 – the linchpin of the operation. These three-digit verification codes serve as the proverbial keys to the kingdom, granting access to a world of illicit transactions. Yet, obtaining valid CVV2 codes is no small feat, requiring skill, patience, and a healthy dose of luck.
For those willing to take the plunge, platforms like bclub.cm offer a glimpse into this clandestine ecosystem. Here, users can browse listings, exchange messages, and engage in transactions with relative ease. But behind the veil of anonymity lies a web of deception, where every interaction carries the risk of exposure.
In the cat-and-mouse game of cybercrime, staying one step ahead is essential. From encryption techniques to stealthy communication channels, participants must employ a myriad of tactics to evade detection and maintain operational security. Yet, as technology evolves and law enforcement agencies bolster their efforts, the stakes continue to rise.
The allure of the dark web is undeniable, drawing in curious bystanders and seasoned criminals alike. But for every success story, there are countless tales of woe – of lives ruined, fortunes lost, and dreams shattered. In this unforgiving landscape, the line between predator and prey blurs, leaving behind a trail of devastation in its wake.
As we peer into the depths of this digital underworld, one thing becomes clear: the allure of easy money comes with a price. For every transaction made, there is a victim left behind, their lives upended by the callous actions of faceless perpetrators. In the battle between good and evil, it falls upon each of us to choose our side wisely – for the consequences of our actions ripple far beyond the confines of cyberspace.