Programming burglary essentially diminishes the reachable pay for programming creators. Programming privateers like to act from countries where legal assist in summoning with reproaching subjects is especially poor to not existent using any and all means, so the item provider remains often unsuitable to approve his grant terms. Today, the best technique dealing with this issue is the coordination of safety frameworks in the item, with the plan to make the item as trying to break as could be anticipated.
Lately, more techniques have been investigated to safeguard programming from burglary by inserting a secret message, the indicated watermarking. This engraving is hidden inside the data of the item. The procedure equips a to some degree strong programming protection in light of the fact that such watermark should be distracted really by someone who has the secret key used for the construction of the Watermark programming. Anyway, a toxic client could pursue the grant part by moving it toward really affirming the presence of a genuine license, whether or not there is none effectively open. Notwithstanding, in this special circumstance, the new developed methods have all the earmarks of being by and large secure.
Creators watermark an item by implanting unique identifiers to state ownership to the genuine proprietor yet notwithstanding track down the privateer after the unlawful show. Along these lines, programming watermarking itself truth be told does similarly hinder burglary by alarming the client from copyright infringement by growing the possibility getting found out. It ought to be referred to that watermarking is most certainly not a fundamental methodology. Most other existing adversary of burglary strategies are easy to do, but their feasibility in preventing robbery is much of the time risky. Moreover, nowadays, various applications are flowed in plans easy to dissect - see Java bytecode and Microsoft Moderate Language - so also by virtue of watermarking, the saltine could decompile or focus on the source code under disassembler as well as debugger to find and wipe out all leftover pieces of the method.
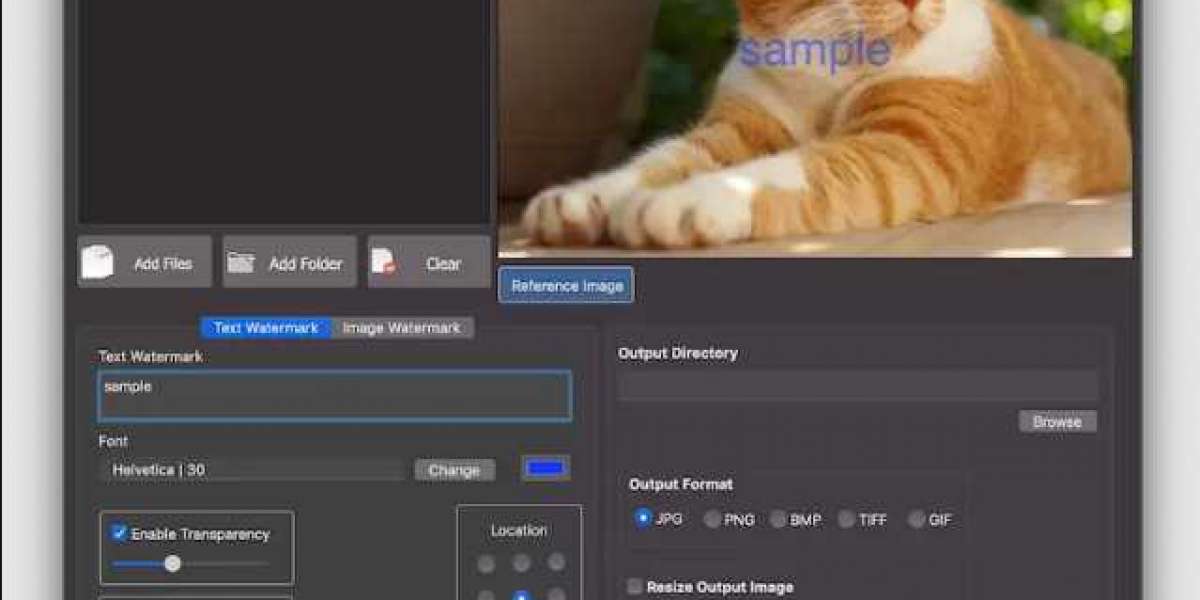
The general idea of Free watermark software is fundamentally equivalent to electronic media watermarking in which an exceptional identifier is embedded in pictures, sound, or accounts. The methodology is applied through the introduction of minor mix-ups which are not remarked by clients. Of course, the watermark can't be applied in programming through bungle causing strategies since programming depends absolutely upon a misstep free convenience.
Along these lines, programming watermarking embeds an exceptional identifier - called the watermark - into a program. In case the identifier curiously spreads out the maker of the program, the identifier is a copyright notice. Regardless, if the identifier extraordinarily perceives the genuine purchaser of the program, the watermark is a finger impression. A huge piece of watermarking is the usage of a secret key. Utilizing the key, the watermark is combined into the program, making a - but insignificantly - different program. Regardless, the person issue go on as in the past: a watermark can exhibit ownership yet it can not feature the certifiable liable party of the criminal behavior. To add such characteristics to the watermark, it transforms into an extraordinary imprint: indeed, the finger impression data is a watermark containing data from the solitary client.
Static watermarks are taken care of in the program twofold itself yet strong watermarks are made at runtime and set aside in program memory. Static programming watermarking is cleaned for a more broadened time span, the strong version was introduced even more lately. The strong watermark is manufactured - while it is executed - inside the continuously circulated data plans of a program. Regardless, an aggressor could apply sorting out to find the watermark making code. He could then discard the making code, in this way dispensing with the watermark from the thing too. For such cases, the suggested use is the special finger impression, an unprecedented variety of watermark. Fingerprinting suggests each individual copy of the item is remarkably watermarked, thusly allowing a conspicuous confirmation of each and every particular copy of an item thing. In that capacity, by the strategy for fingerprinting, each copy of the item is autonomously watermarked, each one containing data featuring its client as opposed to its architect.
All around, watermarking and fingerprinting are astoundingly fruitful in fighting back programming theft. Anyway, the result is fairly defective which makes additional security methodologies are for the most part fitting. Gotten together with other known techniques, breaking such plans ends up being drawn-out to the point that even the cultivated wafer could choose for more straightforward material.
For more information, Visit us:-